The rumor is that the Schools and Libraries Division is considering funding cyber security products and services under E-rate Category 2. If so, you will consider which products to have the government pay for.
You can keep buying more of the same stuff—more firewalls, more client software, and perhaps more cyber security services like remote monitoring of your networks over the Internet, All these products and services are useful; but it may help more to add something different, rather than adding more of the same thing. Consider this alternative:
You have firewalls at your Internet connection and you have security software on your client devices, and when you move servers to the cloud, you expect your cloud service provider to just take control and protect those ‘cloud’ servers. Congratulations! You have protection on all the edges of your networks—but none of this protects your inside networks—once a hacker or malicious package has slipped past your firewall from the Internet in a carefully crafted email, come around the firewall on a thumb drive, or traveled onto your network in an infected PC they can usually live there for a long time and can access the cloud resources just like a regular user. The average ‘dwell’ time of that hacker or malicious application on any inside network is currently four to five months.
Consider different and complementary. So, if you are going to take E-rate up on their security system offer this year or the next year, why not get something different and protect the inside of your networks?
Consider our solution; a Fortune 100-class suite of products downsized for use on a K-12 network. Here’s how it works:
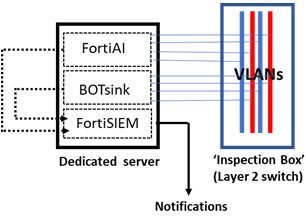
You give us one Layer 2 switch installed in the core of your network, and then you plumb your important networks into that switch. We call it the ‘inspection box’. We will provide and install one server with three applications:
The first application looks at the traffic passing through the VLANs in that Layer 2 switch and uses artificial intelligence to make decisions about whether that traffic is safe or malicious. This application is currently used on worldwide backbone networks to find and categorize attacks there; it has just been downsized to fit your budget. It identifies malicious traffic with a 99.9 percent effectiveness, and it does that within 100 milliseconds.
The second application puts up to 192 lures on the networks passing through the Layer 2 switch. These lures mimic your servers, workstations, and other critical resources embedded on your local networks, or in the cloud. You can even embed ‘gold images’ of your servers and applications to make them indistinguishable from the real resources, so they are indistinguishable from the real things. This application happens to be used by half of the Fortune 100 to protect their networks and servers from attack.
Using two applications to engage the same traffic in the ‘inspection box’ helps insure that all bad actors are found, identified, and then trapped in the system until you can deal with them.
Both applications then send alerts to a third application that consolidates the alerts and forwards them to your designated IT people—when they click the link on the email or text alert they go to that application’s handy console screen that shows the attack or issue, tells them all about that issue, and includes a utility linking to firewalls, switches and wireless access points for one-click remediation of attacks; usually when the attacker is tangled up in one of the many decoys.
Here’s a rough schematic:
Fair warning–you will have to do some work to make this effective—you will have to devote 20 percent of one person’s time to learn this different system and keep up with it. But if you do, you will have at least doubled your existing cyber protection; and at a very moderate cost.
Send an email to sales@mxncorp.com if you’d like to know more.